In the 1983 movie “WarGames,” a young hacker played by Matthew Broderick inadvertently accesses a fictional supercomputer belonging to the U.S. military. Before realizing he has found a system the North American Aerospace Defense Command uses for war simulations, he searches for computer games. The list he gets back starts with classic games like checkers and bridge, but to his surprise, it also includes games called “Guerrilla Engagement” and “Theaterwide Biotoxic and Chemical Warfare.”
Turns out the Department of Defense likes to play computer games in real life too.
More than 40 “security awareness” games are available for anyone to play on the website of the Center for Development of Security Excellence, or CDSE, a directorate within the Defense Counterintelligence and Security Agency, the largest security agency within the U.S. government. The DCSA, which refers to itself as “America’s Gatekeeper,” specializes in security of government personnel and infrastructure as well as counterintelligence and insider threat detection. (The Defense Department did not immediately respond to a request for comment.)
The games range from crossword puzzles and word searches about how to identify an insider threat, to games with more peculiar titles like “Targeted Violence” and “The Adventures of Earl Lee Indicator.” The trove of games looks like an artifact from the late ’90s: game titles announced in WordArt, award badges that look designed with Microsoft Word, “Matrix”-esque backgrounds of falling numbers, and stock photos (some still watermarked).
Some of the games themselves are presented in formats prone to security vulnerabilities. For example, some look like they were made using freely available PowerPoint magic eight ball templates, despite the file format’s potential for containing malware. Playing the magic eight ball games also requires downloading and opening files, exposing players to potentially malicious attachments. Heightening this risk, it appears not all the games have a carefully guarded provenance: The metadata in a magic eight ball game called “Unauthorized Disclosure,” for instance, indicates that the file was originally stored in a personal Dropbox folder.
The games appear to be used for internal training on topics such as cybersecurity and industrial security as well as insider threats and Special Access Programs, security protocols for handling highly classified information. But they can also reveal what actions Defense Department investigators are taught to flag as an insider threat, like plugging in unauthorized USB devices or downloading eyebrow-raising amounts of files all at once. These clues could potentially help whistleblowers avoid detection when leaking government intelligence.
The Intercept played a selection of the Pentagon’s security games. Here’s what the gameplay was like.
Adjudicative Guidelines Word Search
This word search, based off open-sourced code, is ostensibly designed to teach the player about the government’s adjudicative guidelines for determining a person’s eligibility for security clearance. The teaching method is to search a 625-letter grid for words like “sexual” and “criminal.” For example, once you spot “sexual,” a pop-up informs you that “[s]exual behavior that involves a criminal offense … raises questions about an individual’s judgment, reliability, trustworthiness, and ability to protect classified or sensitive information.” Seemingly the Defense Department believes that anyone convicted of a sex crime can’t be trusted to protect sensitive information.
Who Is the Risk?
This game is a cross between “The Dating Game” and “To Catch a Predator,” if the participants were suspected of being insider threats. In an upbeat voiceover, the game show host — or interrogator, who is represented by a $12 stock photo — says, “Welcome to America’s favorite game show: ‘Who Is the Risk?’ Your task in this exercise is to determine which of our guests is most likely to pose an indicator risk to your organization.”

The Department of Defense’s “Who Is the Risk?” game.
Screenshot: The Intercept
One of the contestants admits to just purchasing a Ferrari, while another brags about having high-level government contacts in the European Union. A third admits that they took classified documents home. Add up who has the most checkboxes and you’ve got your perp. Once you’ve identified the correct suspect, the host tells you to “bring these concerns to the appropriate reporting authority,” as one does.
Whodunit Mystery Game

The opening screen for the “Whodunit” game.
Screenshot: The Intercept
The suspect cards include intricate profiles and a number of potential red flags. David Plum, for instance, has “shared that he’s going through a divorce” and is “declining performance evaluations.” Betty Brown has “never taken a polygraph,” and Marge Merlot “frequently travels to several foreign countries.” After pegging the suspect, you can then select a probable location where the data breach occurred, such as in the cubicle farm (which, we’re informed, lacks security cameras) or the sensitive compartmented information facility, a secure facility for handling sensitive information. Finally, you can pick the method the nefarious leaker deployed, such as spillage or a good old-fashioned phishing attack. After you’ve cracked one case, there are six more to try.
Special Access Program Hidden Object Game
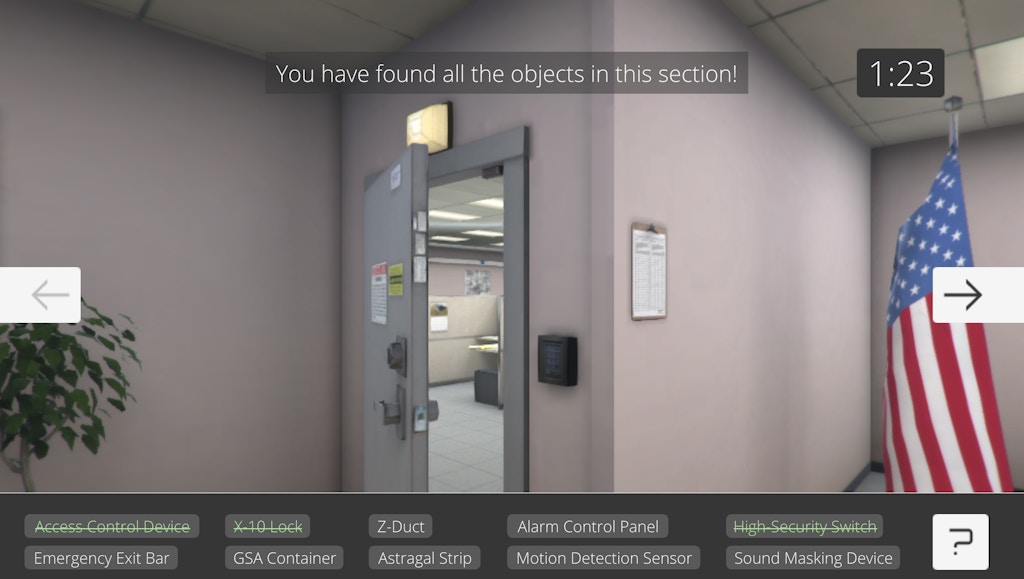
The Special Access Program hidden object game.
Screenshot: The Intercept
This is a standard hidden object game: You have two minutes to locate 10 physical security-related objects. These objects range from General Services Administration containers used for storing classified information, to Z-duct ventilation constructions designed to prevent sound from escaping the secure facility, to astragal strips that can seal gaps in a closed door. If you successfully find all the objects, you’re awarded the rank of “security guru” and unlock a bonus hidden object game, where you now have one minute to find five unauthorized objects, including a personal phone and a wireless keyboard.
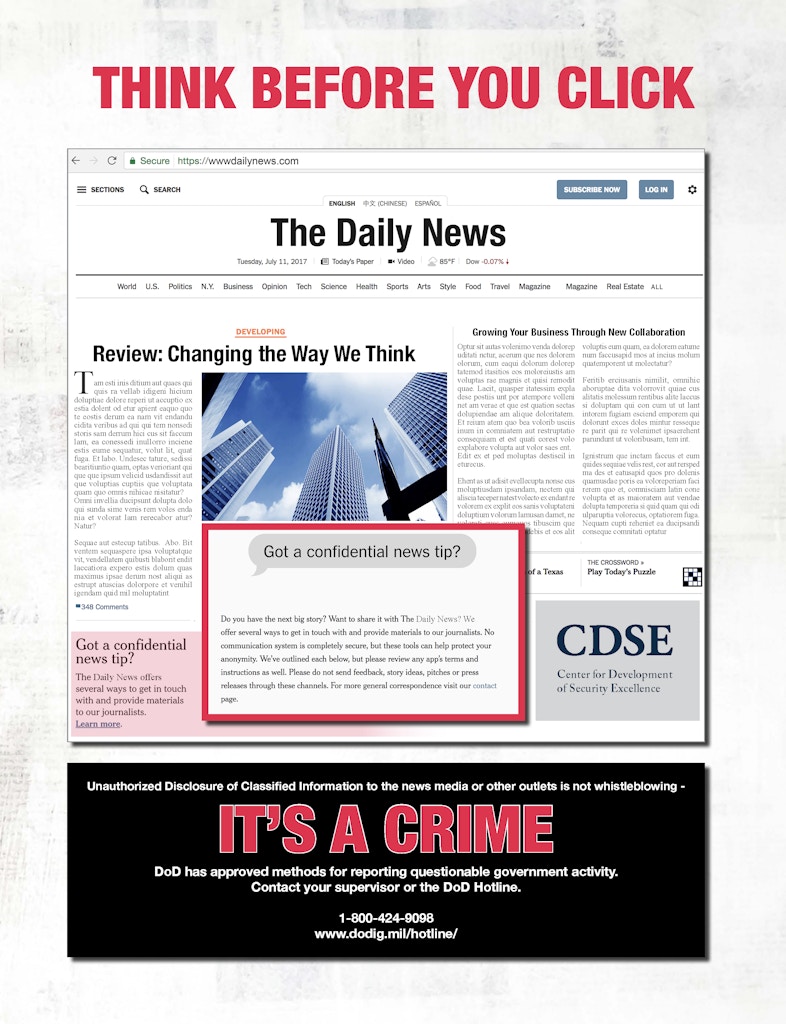
A Department of Defense poster advising against submitting confidential news tips.
Screenshot: The Intercept
If you want to decorate your gaming room to match the Pentagon games as you’re playing, the CDSE also provides over 100 posters about security topics. Many of them are reminiscent of vintage 1960s National Security Agency posters, but others have been updated to warn about modern threats. For instance, one poster depicts a fictitious media outlet called the Daily News; its tips pop-up is verbatim from the New York Times. The poster cautions against following links to submit tips to news media, advising that “unauthorized disclosure of classified information to the news media or other outlets is not whistleblowing” and, in big red letters, “It’s a crime.”
This content originally appeared on The Intercept and was authored by Nikita Mazurov.
Nikita Mazurov | Radio Free (2023-05-02T18:59:31+00:00) The Pentagon Uses Video Games to Teach “Security Excellence.” You Can Play Them Too.. Retrieved from https://www.radiofree.org/2023/05/02/the-pentagon-uses-video-games-to-teach-security-excellence-you-can-play-them-too/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.